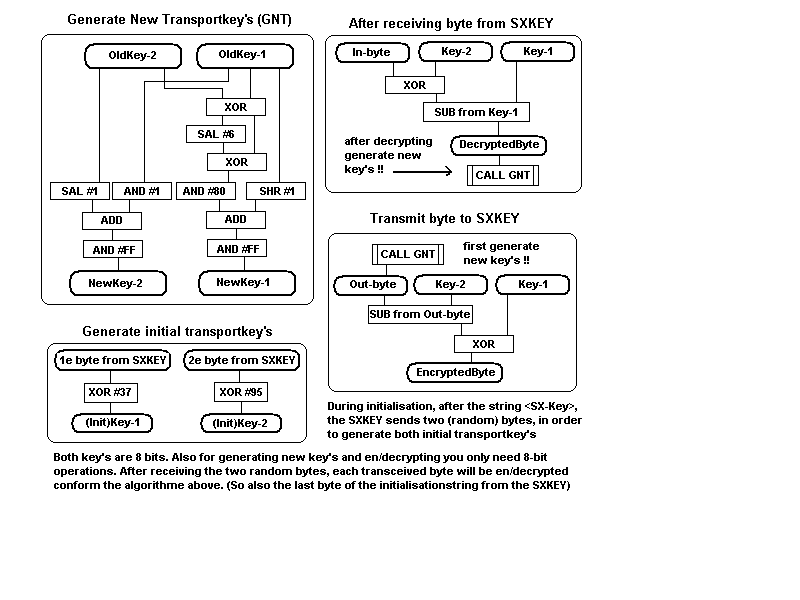
When the owner of a SX-Key likes to approach this unit with his own written software, the SX-Key appears only willing to communicate with encrypted bytes. Fortunately the securety protocol is very simple. You'll need only a few extra instructions.
During initalisation the "real SX-Key" sends two random bytes (in the string wich contains <SX-Key>) to generate the initial transportkey's for the rest of the session. After each transmitted or received byte you have to generate a new pair of key's. (see the scheme).
In the description of the SXBLITZ-protocol the two bytes are fixed: <#37><#95>. Generation of the initial key's from a SXBLITZ always will give 'zero' as outcome for both (also during the rest of the session).
Not described in the document "SXBLITZ Communication Protocol" (In case of programming a real SX-Key): Before sending the words FUSEX and FUSE, send <#02><#32> (of course encrypted!!)
Maarten Mulders [M.J.Mulders at 12move.nl]

Example using good old BASIC
GenKey: 'generate new pair of transportkey's HELP = (((Key1 XOR Key2) * 64) XOR (Key1 XOR Key2)) AND &H80 Key2 = ((Key1 AND 1) + (Key2 * 2)) AND &HFF Key1 = (HELP + INT(Key1 / 2)) AND &HFF: RETURN Decrypt: DecryptByte = (Key1 - (InByte XOR Key2)) AND &HFF: GOSUB GenKey: RETURN Encrypt: GOSUB GenKey: EncryptByte = (Key1 XOR (OutByte - Key2)) AND &HFF: RETURN InitKey: Key1 = Input1 XOR &H37: Key2 = Input2 XOR &H95: RETURN
See also: