Using the Replication Extension Interface
Your DCOM replication extension interface must be developed as detailed in the IMSAdminReplication Interface Reference section and registered with IIS as specified in Custom Extensions Interface. Your interface must be installed on all source and target computers.
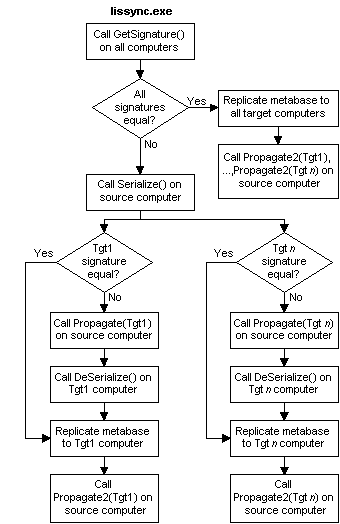
Iissync.exe replicates the metabase and calls system-installed extensions to replicate Web application definitions and MTS application package definitions, adjusting the registry on the target computer as necessary. Iissync.exe also calls your custom replication interface, enabling you to perform additional replication tasks. Your custom replication interface methods are IMSAdminReplication::GetSignature, IMSAdminReplication::Serialize, IMSAdminReplication::DeSerialize, IMSAdminReplication::Propagate, and IMSAdminReplication::Propagate2. Iissync.exe calls all of these methods, if necessary, except Propagate2, before replicating the metabase. It calls your Propagate2 method after replicating the metabase.
When replicating to multiple target computers, iissync.exe processes each target computer independent of the others. This means that different target computers may be in different steps of the replication process at the same time. The process will be discussed in two scenarios: Scenario A, when you replicate from one source computer to one target computer; and Scenario B, when you replicate from one source computer to multiple target computers.
Scenario A:
-
Iissync.exe calls GetSignature on the source and target computers. Both computers calculate and return custom signatures that represent the state of the configuration data and other data that is to be synchronized.
-
Iissync.exe compares the two signatures. If they are the same, iissync.exe replicates the metabase and then calls Propagate2 on the source computer, identifying the target computer and providing a flag that indicates that the signatures were the same. Your program on the source computer can then perform any termination tasks you require.
-
If the two signatures are not the same, iissync.exe calls Serialize on the source computer. Your program returns data to iissync.exe for presentation to the target computer with a call to DeSerialize. Data stored in a secure manner may be transferred with these methods.
-
If the two signatures are not the same, iissync also calls Propagate on the source computer, identifying the target computer and providing a flag indicating that the signatures were different. Your program on the source computer can then transfer data directly to the target computer. For example, you might use xcopy, or some other network copy utility, to copy data files to the target computer from the source computer or from another computer on the network. Serialize and Propagate are called on the source computer before DeSerialize is called on the target computer. Deserialize will not be called on the target computer if either the Serialize or Propagate method returns an error that causes replication to be terminated.
-
Iissync.exe then calls Propagate2 on the source computer, identifying the target computer and providing a flag that indicates the signatures were not the same. Your program on the source computer can then perform any termination tasks you require associated with this target computer.
Scenario B:
-
The process operates exactly the same for each target computer as described in Scenario A.
-
Iissync.exe calls the source computer's GetSignature method only once. The returned signature is compared against each target computer's signature.
-
If any target computer's signature differs from the source computer, iissync.exe calls the source computer's Serialize method once. Your program returns data to iissync.exe for presentation to all target computers that have different signatures. Iissync.exe also calls the Propagate method on the source computer once for each target computer with a signature mismatch. The data returned from the source computer's Serialize method is presented through the DeSerialize method to those target computers that have different signatures. DeSerialize will not be called on the target computer if either the Serialize or Propagate method returns an error that causes replication to be terminated.
-
After iissync replicates the metabase to a target computer, it calls the Propagate2 method on the source computer, identifying the target computer and providing a flag that indicates whether or not this target computer's signature matches the source computer's signature. Iissync.exe calls the source computer's Propagate2 method once for each target computer, regardless of whether the target computer's signature matches the source computer's signature. Propagate2 will not be called on the source computer for any target computer for which the replication process has been terminated by an error.
-
The source computer's Propagate and Propagate2 methods may be called multiple times in no predictable sequence, except that Propagate2 is called when the replication process is complete for the identified target computer.
Note Replication to multiple target computers is not sequenced. You should not make any assumptions when designing your program in regards to the order in which target computers are selected for replication. Your GetSignature method is called first. On the source computer, calls to other methods may be received multiple times in any order.
Replication Process Flow
© 1997 by Microsoft Corporation. All rights reserved.

